eduffield
Core Developer
Darksend+ Progress:
We’re making steady progress on Darksend+ and testing is coming closer to an end.
The GUI now supports sending any amount instantly and anonymously. All you have to do is let the client automatically denominate your funds by leaving it open. Currently mixing depth can be configured with a command line option, but a configuration option in the GUI will be added as work progresses.
The user now has the option to select whether not they would like to send only coins which have been anonymized by Darksend+, only coins which have NOT been anonymized by Darksend+, or a mix of both.

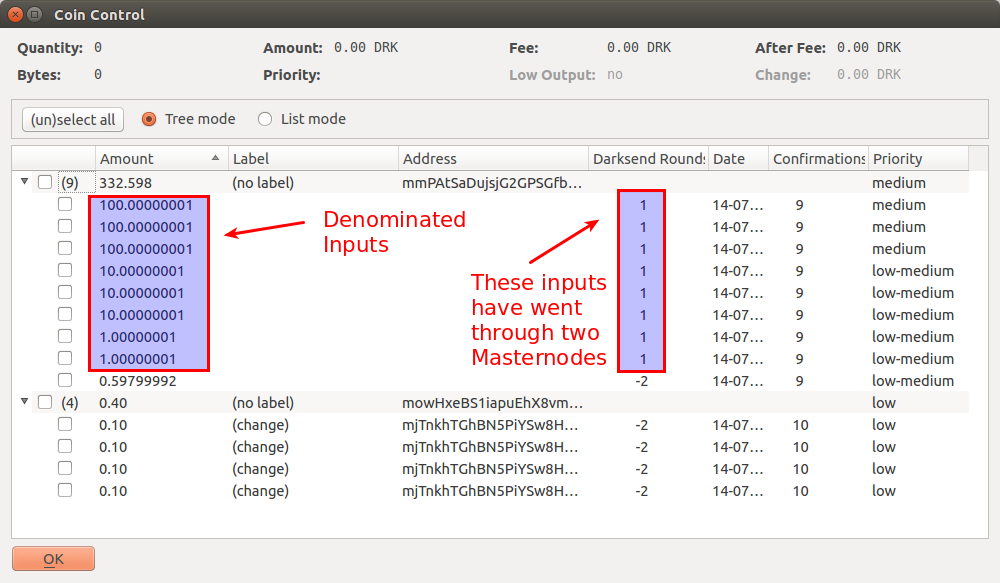
Using coincontrol, you can now see how many times specific inputs have passed through the Darksend process:
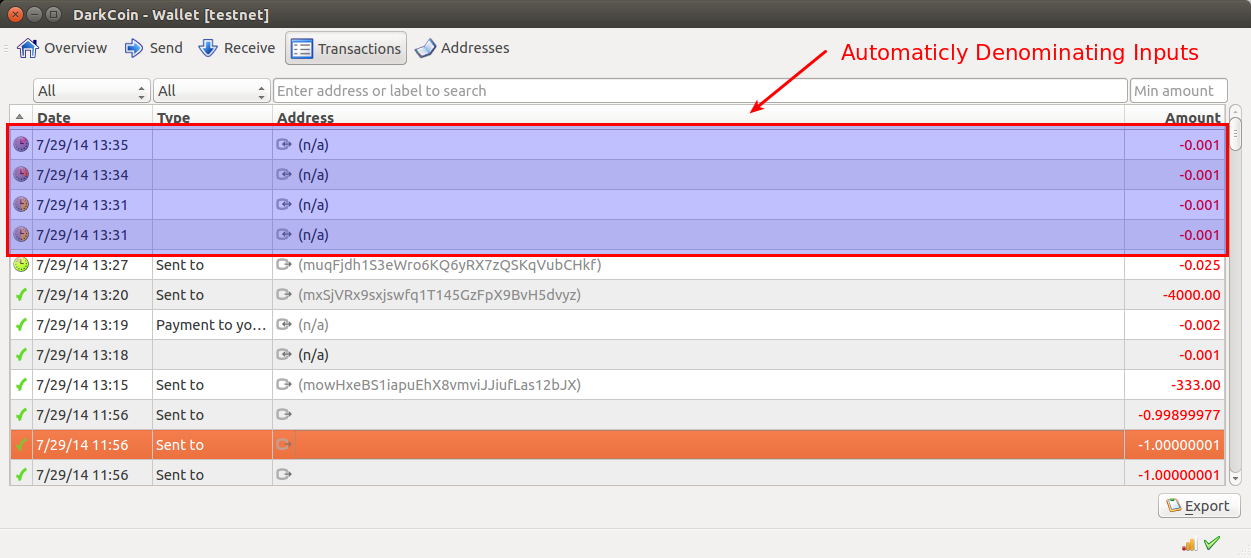
Here you can see the client automatically denominating money:
We’re in the process of removing all of the bugs in the software. This was a complete rewrite of the system, which has put us slightly behind schedule for release (a complete rewrite was not what we originally intended to do). As it stands currently, we have a few issues left to address before we can release RC4 on mainnet:
Considering all of the work that needs to be done, we’re looking at a release in early August.
IP Obfuscation:
IP Obfuscation is a critical part of the anonymity package that Darkcoin will bring to bear. Though completion and release of RC4 is our primary concern at the moment, we do have a working roadmap for the implementation of IP obfuscation.
Here’s how it works:
Anyone on the Darkcoin network will be able to communicate securely by using the Masternode network and our encrypted transit system. A user who would like to transmit a payment securely will encrypt the message in such a way that only specific Masternodes can decrypt it.
The user’s client will select three Masternodes, then use the privkey from each of those nodes to wrap the message it wishes to send in three successive encrypted containers. These containers can only be decrypted by their associated Masternodes.
Once wrapped in these three containers, the client will send the encrypted package to the Masternode that corresponds to the outermost encryption layer (Masternode 1). Upon receiving it, Masternode 1 will decrypt the outermost layer in order to learn the identity of the second Masternode in the sequence. Masternode 1 will then relay the message to Masternode 2, which will decrypt the 2nd encryption layer and learn the identity of the third Masternode in the sequence. Masternode 2 forwards the package on to Masternode 3, which decrypts the innermost encryption layer, gaining access to message itself. Masternode 3 then broadcasts the message to the network, and far as the network is concerned, that is where the message originated.

With this envelope encryption system, Masternode 1 is not able to determine which Masternode will ultimately broadcast the message. Similarly, Masternode 3 is unable to determine the identity of either the first Masternode in the sequence or of the original sender.
Darkcoin.io Overhaul:
We’ve been looking at ways to keep the official website darkcoin.io more up to date. Fernando (from the darkcointalk boards) is heading up an effort to overhaul the site, with the following goals in mind:
Wallet Overhaul:
DRKLord, Minotaur, Raze et al continue their efforts on refinement of the Darkcoin wallet UI, and they are closing in on a completed design. Its release will likely be separate from RC4. You can follow their efforts and offer your feedback here: http://goo.gl/1yFUEb.
We’re making steady progress on Darksend+ and testing is coming closer to an end.
The GUI now supports sending any amount instantly and anonymously. All you have to do is let the client automatically denominate your funds by leaving it open. Currently mixing depth can be configured with a command line option, but a configuration option in the GUI will be added as work progresses.
The user now has the option to select whether not they would like to send only coins which have been anonymized by Darksend+, only coins which have NOT been anonymized by Darksend+, or a mix of both.
Using coincontrol, you can now see how many times specific inputs have passed through the Darksend process:
Here you can see the client automatically denominating money:
We’re in the process of removing all of the bugs in the software. This was a complete rewrite of the system, which has put us slightly behind schedule for release (a complete rewrite was not what we originally intended to do). As it stands currently, we have a few issues left to address before we can release RC4 on mainnet:
- Ensure that Darksends have at least 1 of each input and so that unique change addresses are used, further improving anonymity
- Add functionality for locked wallets to prompt the user to temporarily decrypt the wallet so that funds can be denominated
- Daemons need to deal with encrypted wallets
- Rewrite all functions that send money so that they only use denominated money or non-denominated money
- Track down an unknown bug causing Darksend collateral to be taken from users during the auto-denomination process. Darksend uses collateral to prevent malicious users from joining a Darksend transaction and then failing to sign. In this case, the client is refusing to sign because it believes there is missing data in the transaction when there is not (or the Masternode is not compiling the transaction correctly and the user is correct not to sign).
- Complete testing on the Masternode voting system
- Add auto-detection of wallets from pools and exchanges in order to disable Darksend
Considering all of the work that needs to be done, we’re looking at a release in early August.
IP Obfuscation:
IP Obfuscation is a critical part of the anonymity package that Darkcoin will bring to bear. Though completion and release of RC4 is our primary concern at the moment, we do have a working roadmap for the implementation of IP obfuscation.
Here’s how it works:
Anyone on the Darkcoin network will be able to communicate securely by using the Masternode network and our encrypted transit system. A user who would like to transmit a payment securely will encrypt the message in such a way that only specific Masternodes can decrypt it.
The user’s client will select three Masternodes, then use the privkey from each of those nodes to wrap the message it wishes to send in three successive encrypted containers. These containers can only be decrypted by their associated Masternodes.
Once wrapped in these three containers, the client will send the encrypted package to the Masternode that corresponds to the outermost encryption layer (Masternode 1). Upon receiving it, Masternode 1 will decrypt the outermost layer in order to learn the identity of the second Masternode in the sequence. Masternode 1 will then relay the message to Masternode 2, which will decrypt the 2nd encryption layer and learn the identity of the third Masternode in the sequence. Masternode 2 forwards the package on to Masternode 3, which decrypts the innermost encryption layer, gaining access to message itself. Masternode 3 then broadcasts the message to the network, and far as the network is concerned, that is where the message originated.
With this envelope encryption system, Masternode 1 is not able to determine which Masternode will ultimately broadcast the message. Similarly, Masternode 3 is unable to determine the identity of either the first Masternode in the sequence or of the original sender.
Darkcoin.io Overhaul:
We’ve been looking at ways to keep the official website darkcoin.io more up to date. Fernando (from the darkcointalk boards) is heading up an effort to overhaul the site, with the following goals in mind:
- Move the site from Github to Wordpress
- Bring the theme in line with current Darkcoin properties
- Engage more people to maintain and update the website. By using Wordpress, we hope to enable non-developers to work on the site so that devs can concentrate on coding Darkcoin.
- Streamline the overall structure of darkcoin.io
- Aim for release of the new site with a timescale measured in weeks vs. months
Wallet Overhaul:
DRKLord, Minotaur, Raze et al continue their efforts on refinement of the Darkcoin wallet UI, and they are closing in on a completed design. Its release will likely be separate from RC4. You can follow their efforts and offer your feedback here: http://goo.gl/1yFUEb.
