Antti Kaikkonen
Active member
The goal of this project is to measure how private PrivateSend is
How:
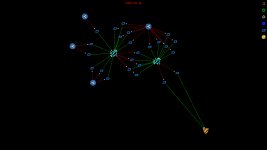
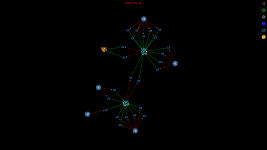
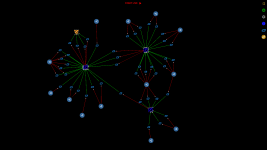
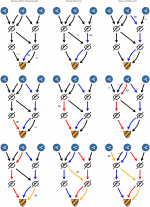
For a given PrivateSend transaction with k inputs
I have already completed step 1. I also created an algorithm for step 2, but I haven't tested it with real data yet. I think it will be possible compute all the combinations for a small number of rounds but it might be computationally infeasible if we have many inputs combined with for example 8 rounds.
- for different number of rounds
- for different number of inputs in a PrivateSend transaction
- on average
- in the worst case (can we identify PrivateSend transactions with weak privacy)
How:
For a given PrivateSend transaction with k inputs
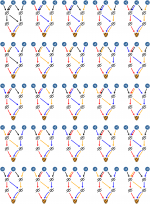
- Find all paths from the PrivateSend transaction to all create denominations transactions that can be reached after a given number of mixing rounds
- Find all k-combinations of paths such that in each combination the paths are not allowed to contain same transaction outputs
- Now we have all possible mixing combinations for the PrivateSend transaction and we can start analysing the combinations.
- If we find zero combinations then we can conclude that the PrivateSend transaction didn't use the number of rounds we assumed
- If we have 1 combination then the PrivateSend transaction wasn't private for the assumed number of rounds (but it could be private for a different number of rounds)
- If we find that in all of the combinations one of the PrivateSend inputs always maps to the same create denominations transaction then the PrivateSend transaction wasn't private for the assumed number of rounds (but it could be private for a different number of rounds)
- We could also count the number of possible wallets for each of the PrivateSend inputs and use the minimum as a measure of how private the transaction was
I have already completed step 1. I also created an algorithm for step 2, but I haven't tested it with real data yet. I think it will be possible compute all the combinations for a small number of rounds but it might be computationally infeasible if we have many inputs combined with for example 8 rounds.
Last edited: