Antti Kaikkonen
Active member
Quote from the blockski paper: "The intuition behind the attack is that outputs mixed in different transactions are often spent together. Thus, when these coins are spent together, we trace each one back to a (potentially large) set of possible address clusters and examine the intersection of these sets. This will likely result in a unique cluster. We conclude that the mixed outputs are linked to the wallet represented by this cluster."
But I don't understand the assumption that if the if the intersection matches an unique address cluster then that would mean that it's the sender. Below is a counter example that I tried to make using only 1 round of mixing:
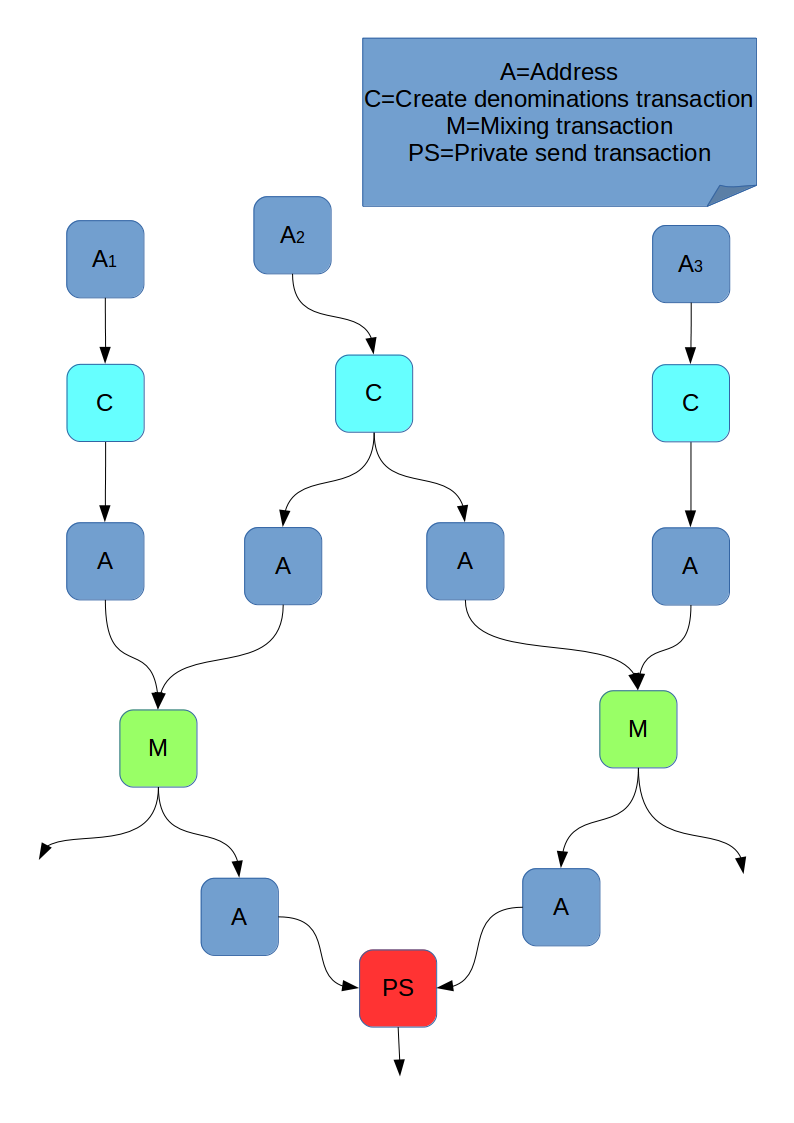
Based on my understanding of the cluster intersection attack it would select A2 as the source address because it is reachable from both privatesend inputs. Why aren't A1 and A3 also valid candidates?
But I don't understand the assumption that if the if the intersection matches an unique address cluster then that would mean that it's the sender. Below is a counter example that I tried to make using only 1 round of mixing:
Based on my understanding of the cluster intersection attack it would select A2 as the source address because it is reachable from both privatesend inputs. Why aren't A1 and A3 also valid candidates?
