This was my question, how does cryptonote work? And below is my attempt to answer it from the input I received from some very nice people, thank you!
Edit: I'm including here input from people working on projects that use cryptonote as they understand it best. The purpose of this thread is to understand Cryptonote and it's applications and possibly applications that might be useful to DASH. Every solution has it's flaws but often, you can find a better use for certain techniques when applied to a different problem, so I feel the more people that learn about these techniques, the more great ideas will come out to the surface
These are quotes from luigi1111 on Bitcointalk.org. He was so nice to take the time to help me. I wanted to understand how cryptonote worked and these are the PMs he sent me. He said I could share
Hello,
I read a few of your posts in the Peter Todd thread, and I think I can maybe help you out with understanding Cryptonote a bit.
You talked about tracing coins back to their source, and how you couldn't see how to do that in Cryptonote; that it seemed obscured and required trust.
If you look here: http://chainradar.com/bcn/transacti...2e309e9a458a5e03b31cf0d617e4129ca070681a54967 (that's a Bytecoin tx) you can see it has a "From transaction" link; this functions essentially identically to Bitcoin. This link exists because that particular TX was mixin=0, so no ring signature partners were chosen.
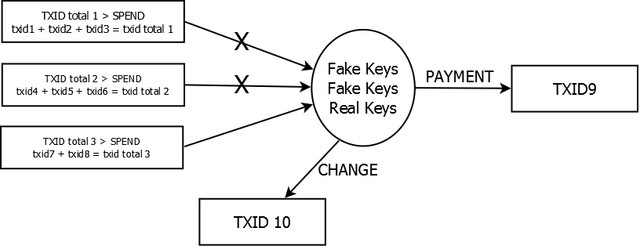
Consider if partners are chosen: there exists a number ( = mixin) of potential inputs that are equiprobable of being the one that was actually spent. In this case, chainradar has no "From transaction" link, because there is more than one possibility. They *could* list all the possible transactions, but they haven't implemented that for whatever reason. Moneroblocks similarly doesn't show previous transactions at all, even for mixin=0. This is only cosmetic, and on the actual blockchain you can be sure that all potential inputs are properly validated and accounted for.
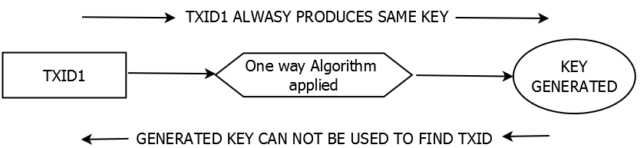
Having the capability to "pretend" to spend others' inputs autonomously would cause you to be able to doublespend; Cryptonote gets around this by using "key images", which cannot be faked, but also cannot be traced back to the input they belong to.
Back to BTC-style transactions for a minute, whenever you group sign (as in, use multiple inputs), you obscure the outputs' origin; assuming size of outputs is less than inputs, any of the inputs could be the source of the funds for the outputs. In effect, you're getting two (or more) possible paths for the coins to have originated from.
This is technically different, but functionally somewhat similar to, the way ring signatures work.
Hope this helps!
luigi1111
Quote from: TanteStefana2 on Today at 05:09:35 PM
Thank you very much for that! I wasn't getting any help anywhere else, LOL. I'm still not clear on everything, and I suspect I need to study a flow chart at this point, which I'm sure exists. That the key signature can't be traced backward worries me because I just don't see how it can be verified to belong to actual coins and not counterfeited coins. I'm sure I'm missing something, it can take me a while of digesting to get that lightbulb moment

Seriously, thank you for taking the time. May I post your explanation in my dashtalk forum thread? Thanks again

Sure, I don't mind.
You know the inputs belong to actual coins because they do point back to previous transactions (this just isn't visible on the current explorers).
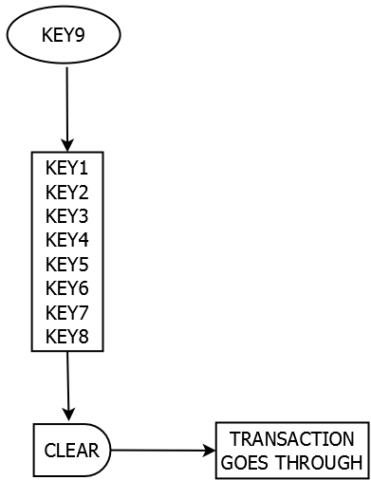
The final "key" piece is the key image. Basically one must be included for every input that is spent. A ring signature identifies which inputs *could* have been spent. The key image "identifies" the input that is *actually* spent, and therefore cannot be "respent", because the key image is unfakeable and would be duplicated. However, the "magic" of ring signatures means only the spender can normally know which input was actually spent.
Instead of marking outputs as spent like in Bitcoin, in Cryptonote a list of all key images ever used is kept to prevent double-spending.
Activity: 532



Trust: 0: -0 / +0
Re: (No subject)
« Sent to: TanteStefana2 on: Today at 06:00:54 PM »
« You have forwarded or responded to this message. »
 Quote
Quote  Reply
Reply  Delete
Delete
Quote from: TanteStefana2 on Today at 05:44:34 PM
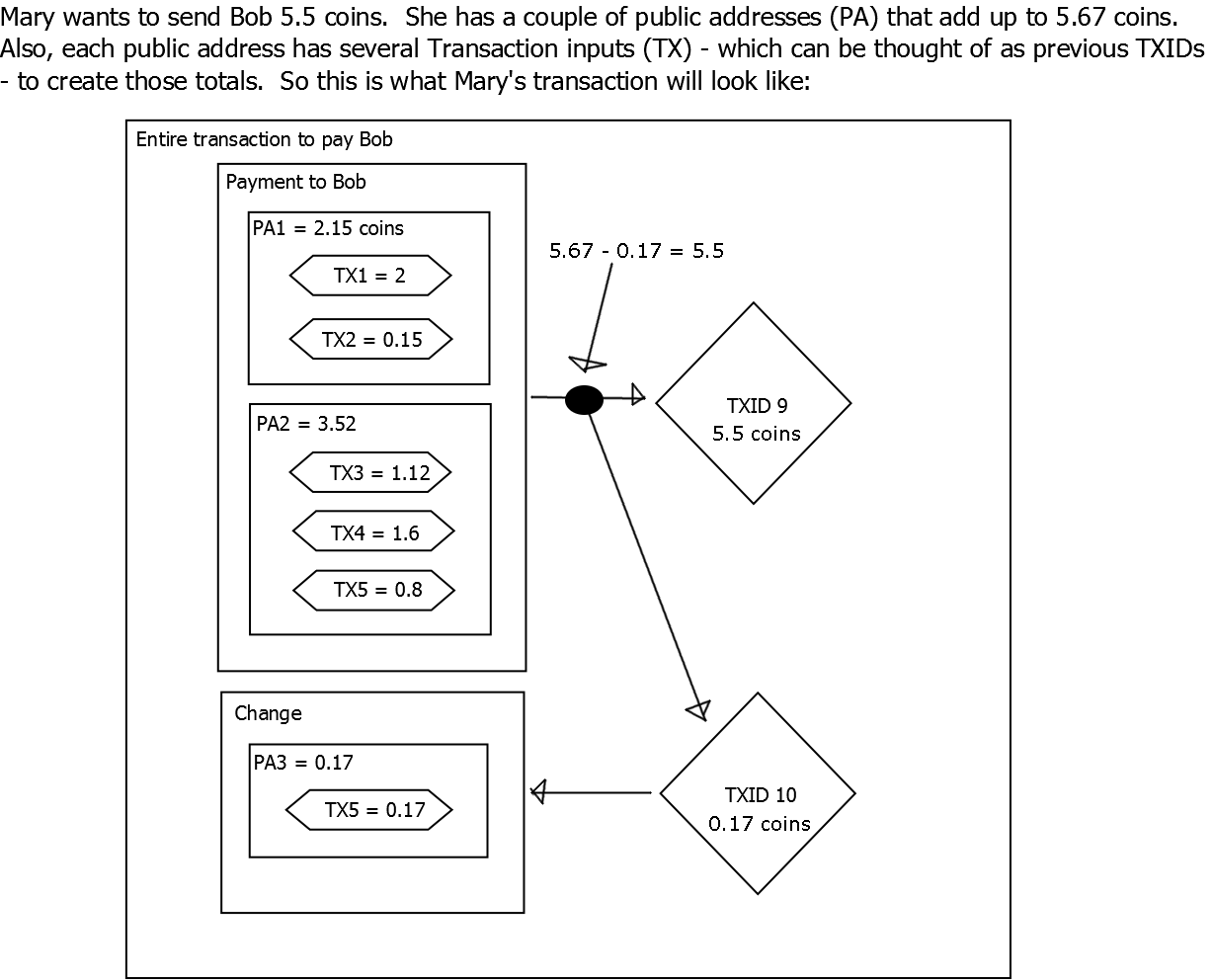
Oh, I just thought of another question. I just can't find simple enough diagrams to help me understand. I'm wondering about change. If Peter Paul and Mary are signers for a transaction, and each one, I presume, must have funds that are possible inputs, how is the change handled?
I know I'm missing something, but you seem to be able to explain very well
 Can't let you go while I have you
Can't let you go while I have you
 LOL.
LOL.
Thanks again, you're such a nice person to take the time for an old lady!
Typically only one party would be a signer of a transaction. If there were say 3 parties, they'd all have to agree on the outputs (ie, change) before signing. I don't think a multiparty TX has ever been done in Cryptonote, though it should be possible.
Edit: I'm including here input from people working on projects that use cryptonote as they understand it best. The purpose of this thread is to understand Cryptonote and it's applications and possibly applications that might be useful to DASH. Every solution has it's flaws but often, you can find a better use for certain techniques when applied to a different problem, so I feel the more people that learn about these techniques, the more great ideas will come out to the surface
These are quotes from luigi1111 on Bitcointalk.org. He was so nice to take the time to help me. I wanted to understand how cryptonote worked and these are the PMs he sent me. He said I could share
Hello,
I read a few of your posts in the Peter Todd thread, and I think I can maybe help you out with understanding Cryptonote a bit.
You talked about tracing coins back to their source, and how you couldn't see how to do that in Cryptonote; that it seemed obscured and required trust.
If you look here: http://chainradar.com/bcn/transacti...2e309e9a458a5e03b31cf0d617e4129ca070681a54967 (that's a Bytecoin tx) you can see it has a "From transaction" link; this functions essentially identically to Bitcoin. This link exists because that particular TX was mixin=0, so no ring signature partners were chosen.
Consider if partners are chosen: there exists a number ( = mixin) of potential inputs that are equiprobable of being the one that was actually spent. In this case, chainradar has no "From transaction" link, because there is more than one possibility. They *could* list all the possible transactions, but they haven't implemented that for whatever reason. Moneroblocks similarly doesn't show previous transactions at all, even for mixin=0. This is only cosmetic, and on the actual blockchain you can be sure that all potential inputs are properly validated and accounted for.
Having the capability to "pretend" to spend others' inputs autonomously would cause you to be able to doublespend; Cryptonote gets around this by using "key images", which cannot be faked, but also cannot be traced back to the input they belong to.
Back to BTC-style transactions for a minute, whenever you group sign (as in, use multiple inputs), you obscure the outputs' origin; assuming size of outputs is less than inputs, any of the inputs could be the source of the funds for the outputs. In effect, you're getting two (or more) possible paths for the coins to have originated from.
This is technically different, but functionally somewhat similar to, the way ring signatures work.
Hope this helps!
luigi1111
Quote from: TanteStefana2 on Today at 05:09:35 PM
Thank you very much for that! I wasn't getting any help anywhere else, LOL. I'm still not clear on everything, and I suspect I need to study a flow chart at this point, which I'm sure exists. That the key signature can't be traced backward worries me because I just don't see how it can be verified to belong to actual coins and not counterfeited coins. I'm sure I'm missing something, it can take me a while of digesting to get that lightbulb moment

Seriously, thank you for taking the time. May I post your explanation in my dashtalk forum thread? Thanks again

Sure, I don't mind.
You know the inputs belong to actual coins because they do point back to previous transactions (this just isn't visible on the current explorers).
The final "key" piece is the key image. Basically one must be included for every input that is spent. A ring signature identifies which inputs *could* have been spent. The key image "identifies" the input that is *actually* spent, and therefore cannot be "respent", because the key image is unfakeable and would be duplicated. However, the "magic" of ring signatures means only the spender can normally know which input was actually spent.
Instead of marking outputs as spent like in Bitcoin, in Cryptonote a list of all key images ever used is kept to prevent double-spending.
Activity: 532

Trust: 0: -0 / +0
Re: (No subject)
« Sent to: TanteStefana2 on: Today at 06:00:54 PM »
« You have forwarded or responded to this message. »
 Quote
Quote  Reply
Reply  Delete
DeleteQuote from: TanteStefana2 on Today at 05:44:34 PM
Oh, I just thought of another question. I just can't find simple enough diagrams to help me understand. I'm wondering about change. If Peter Paul and Mary are signers for a transaction, and each one, I presume, must have funds that are possible inputs, how is the change handled?
I know I'm missing something, but you seem to be able to explain very well


Thanks again, you're such a nice person to take the time for an old lady!
Typically only one party would be a signer of a transaction. If there were say 3 parties, they'd all have to agree on the outputs (ie, change) before signing. I don't think a multiparty TX has ever been done in Cryptonote, though it should be possible.
Last edited by a moderator: