https://99bitcoins.com/anonymity-cryptocurrencies-2-cryptonote/
BY COINBRIEF ON SEPTEMBER 27, 2014 - UPDATED ON SEPTEMBER 27TH, 2014 ALTCOIN, BITCOIN, FEATURED, WHAT IS ****COIN?
Although total anonymity is not feasible at the moment, a lesser form of high security may be. Cryptonote-based currencies can use ring signatures, as opposed to group signatures which require a trusted party. Each transaction with Bitcoin has a public key tied to it which requires a small script to be produced to spend the output using that key. When people view this transaction they see that the old output is used and that new outputs have been created.
What Are Ring Signatures?
Ring signatures are different. They are tied to an arbitrary group of public keys and only one needs to be known to sign the transaction. Cryptonote does this by having every transaction input actually be a set of unspent outputs of that same value, signing it using all those outputs’ keys. This makes it impossible to differentiate transactions and uncover who is the actual signer. Whilst this technology is sound, not every implementation is. Boolberry and Monero are the only two working, sound implementations, with alternatives like Bytecoin not being worthwhile.
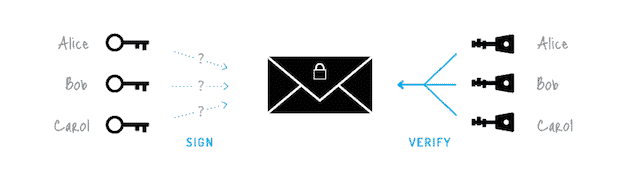
An example of ring signatures being implemented in Bitmonero, a fork of Bytecoin.
The question arises, if it is not possible to uncover which outputs are spent, how can the system prevent scammers from double-spending the same outputs? A special algorithm has the actual signing key imprinted with a key image that must be published when the signature is. This cannot be reversed to find the original key or de-anonymize the sender, however, it allows users to see a reused key image and choose not to participate in the scam transaction.
The Technical Potential of Cryptonote
Cryptonote is one of the strongest options, however, it is not totally zero-knowledge. An especially determined investigator may still be able to uncover an identity due to the small amount of information input by the user. It is an extremely useful advancement, with problems that are mostly fixable. Scalability is a large issue, as ordinary Bitcoin stores the total list of unspent outputs on a node with limited storage. Cryptonote stores all of this on RAM, which severely limits its potential to scale. This can be changed through forcing users to store only outputs of the keys they own and a few others to remain anonymous. Improving on this system allows for the equivalent of CoinJoin-ing all transactions in every block, with the exceptions that a miner could de-anonymize the CoinJoin and it is not possible for Cryptonote to detect a cheating miner.
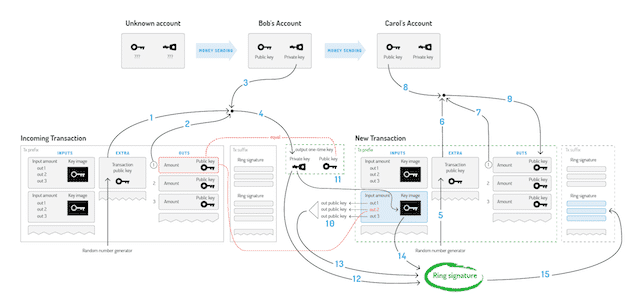
This diagram shows how Cryptonote uses complex ring signatures to achieve anonymity.
Another issue is that anonymity might be compromised by others in the set, outputting a ring signature with two other outputs may see the other two output owners spending their funds with a single signature. This makes it possible to know who spent their funds, since each output can only be used once, and this can be done long after the transaction occurs. Two out of three individuals confirmed to have spent leaves only one individual unspent, compromising security through potential identification. A possible solution is having Cryptonote require a minimum size of a set.
However, that leads to another problem — only so many outputs of any size can exist, and all outputs in an anonymous set must be the same size so that the network can determine how much is being spent. Solving this would require allowing outputs of any size in each anonymous set, then taking the minimum size to be the spent amount. The potential for the smallest size user to be uncovered is also a real threat, since each Cryptonote output can only be spent once. A solution exists where every single output can be read as a single, uniform, distribution of outputs. One might spend half a Bitcoin, and two might spend three .33 of a Bitcoin, the network would add it as one total Bitcoin. A feasible anonymous set size is possible with this system, though it is possible to be compromised by certain users revealing their secret keys, however there is no known way to prevent that on any system.
Anonymity Via Darkcoin
Darkcoin operates like a somewhat broken version of CoinJoin on the normal Bitcoin client. DarkSend+sees the possibility of anonymizing all coins automatically at an interval, not just when they are sent, leaving the entire corpus of coins as anonymous values. The masternode system would also tie multiple DarkSend passes together to increase security, allowing for security even if certain nodes are compromised. It could see serious benefit later on, however, until serious technological innovations are made, alt-coin security systems have serious fundamental issues.
BY COINBRIEF ON SEPTEMBER 27, 2014 - UPDATED ON SEPTEMBER 27TH, 2014 ALTCOIN, BITCOIN, FEATURED, WHAT IS ****COIN?
Although total anonymity is not feasible at the moment, a lesser form of high security may be. Cryptonote-based currencies can use ring signatures, as opposed to group signatures which require a trusted party. Each transaction with Bitcoin has a public key tied to it which requires a small script to be produced to spend the output using that key. When people view this transaction they see that the old output is used and that new outputs have been created.
What Are Ring Signatures?
Ring signatures are different. They are tied to an arbitrary group of public keys and only one needs to be known to sign the transaction. Cryptonote does this by having every transaction input actually be a set of unspent outputs of that same value, signing it using all those outputs’ keys. This makes it impossible to differentiate transactions and uncover who is the actual signer. Whilst this technology is sound, not every implementation is. Boolberry and Monero are the only two working, sound implementations, with alternatives like Bytecoin not being worthwhile.

An example of ring signatures being implemented in Bitmonero, a fork of Bytecoin.
The question arises, if it is not possible to uncover which outputs are spent, how can the system prevent scammers from double-spending the same outputs? A special algorithm has the actual signing key imprinted with a key image that must be published when the signature is. This cannot be reversed to find the original key or de-anonymize the sender, however, it allows users to see a reused key image and choose not to participate in the scam transaction.
The Technical Potential of Cryptonote
Cryptonote is one of the strongest options, however, it is not totally zero-knowledge. An especially determined investigator may still be able to uncover an identity due to the small amount of information input by the user. It is an extremely useful advancement, with problems that are mostly fixable. Scalability is a large issue, as ordinary Bitcoin stores the total list of unspent outputs on a node with limited storage. Cryptonote stores all of this on RAM, which severely limits its potential to scale. This can be changed through forcing users to store only outputs of the keys they own and a few others to remain anonymous. Improving on this system allows for the equivalent of CoinJoin-ing all transactions in every block, with the exceptions that a miner could de-anonymize the CoinJoin and it is not possible for Cryptonote to detect a cheating miner.

This diagram shows how Cryptonote uses complex ring signatures to achieve anonymity.
Another issue is that anonymity might be compromised by others in the set, outputting a ring signature with two other outputs may see the other two output owners spending their funds with a single signature. This makes it possible to know who spent their funds, since each output can only be used once, and this can be done long after the transaction occurs. Two out of three individuals confirmed to have spent leaves only one individual unspent, compromising security through potential identification. A possible solution is having Cryptonote require a minimum size of a set.
However, that leads to another problem — only so many outputs of any size can exist, and all outputs in an anonymous set must be the same size so that the network can determine how much is being spent. Solving this would require allowing outputs of any size in each anonymous set, then taking the minimum size to be the spent amount. The potential for the smallest size user to be uncovered is also a real threat, since each Cryptonote output can only be spent once. A solution exists where every single output can be read as a single, uniform, distribution of outputs. One might spend half a Bitcoin, and two might spend three .33 of a Bitcoin, the network would add it as one total Bitcoin. A feasible anonymous set size is possible with this system, though it is possible to be compromised by certain users revealing their secret keys, however there is no known way to prevent that on any system.
Anonymity Via Darkcoin
Darkcoin operates like a somewhat broken version of CoinJoin on the normal Bitcoin client. DarkSend+sees the possibility of anonymizing all coins automatically at an interval, not just when they are sent, leaving the entire corpus of coins as anonymous values. The masternode system would also tie multiple DarkSend passes together to increase security, allowing for security even if certain nodes are compromised. It could see serious benefit later on, however, until serious technological innovations are made, alt-coin security systems have serious fundamental issues.
